Cara Sql Injection Manual
SQL Injection Examples and ways to prevent SQL Injection Attacks on Web Applications:While testing a website or a system, the tester's aim is to ensure if that tested product is as much protected, as possible.Security testing is usually performed for this purpose. In order to perform this type of testing, initially, we need to consider, which attacks are most likely to happen. SQL Injection is one of those attacks.SQL Injection is considered as one of the most common attacks as it can bring serious and harmful consequences to your system and sensitive data. What You Will Learn:.What is SQL injection?Some of the user inputs might be used in framing that are then executed by the application on the database. It is possible for an application NOT to handle the inputs given by the user properly.
Cara Hacking Website Dengan Teknik Manual SQL Injection Onix AQua 9:11 AM Defacing, 20 Comments Pengertian SQL Injection SQL Injection merupakan sebuah teknik hacking dimana seorang penyerang dapat memasukkan perintah-perinta. Pengertian sql injection: SQL injection adalah sebuah aksi hacking yang dilakukan di aplikasi client dengan cara memodifikasi perintah SQL yang ada di memori aplikasi clien dan juga merupakan teknik mengeksploitasi web aplikasi yang didalamnya menggunakan database untuk penyimpanan data. Yang perlu di ketahui sebelum sql injection pada mysql. Cara Hacking Website Dengan Teknik Manual SQL Injection Onix AQua 9:11 AM Defacing, 20 Comments Pengertian SQL Injection SQL Injection merupakan sebuah teknik hacking dimana seorang penyerang dapat memasukkan perintah-perinta.
If this is the case, a malicious user could provide unexpected inputs to the application that are then used to frame and execute SQL statements on the database. This is called SQL injection. The consequences of such an action could be alarming.As the name itself implies, the purpose of SQL Injection attack is to inject the malicious SQL code.Each and every field of a website is like a gate to the database. In the login form, the user enters the login data, in the search field the user enters a search text, in the data saving form the user enters data to be saved. All these indicated data goes to the database.Instead of correct data, if any malicious code is entered, then there are possibilities for some serious damage to happen to the database and the whole system.SQL Injection is performed with SQL programming language. SQL (Structured Query Language) is used for managing the data held in the database.
Therefore during this attack, this programming language code is being used as a malicious injection.This is one of the most popular attacks, as databases are used for almost all the technologies.Many applications use some type of a database. An application under test might have a user interface that accepts user input that is used to perform the following tasks:#1) Show the relevant stored data to the user e.g. The application checks the credentials of the user using the login information entered by the user and exposes only the relevant functionality and data to the user#2) Save the data entered by the user to the database e.g. Once the user fills up a form and submits it, the application proceeds to save the data to the database; this data is then made available to the user in the same session as well as in subsequent sessions Risks of SQL InjectionNowadays, a database is being used for almost all the systems and websites, as data should be stored somewhere.As the sensitive data is being stored in the database, there are more risks involved for the system’s security. For Example, if get an error message like ‘Internal Server Error‘ as a search result, then we can be sure, that this attack is possible in that part of the system.Other results, that can notify possible attack include:.
Blank page loaded. No error or success messages – functionality and page do not react to the input.
Sql Injection Prevention
Success message for malicious code.Let's look around at how this works in practice.For Example: Let's test if an appropriate login window is vulnerable for SQL Injection. For this purpose, in the email address or password field we just type ‘ sign as shown below.If such input returns result like error message ‘Internal Server Error‘ or any other listed inappropriate result, then we can almost be sure, that this attack is possible for that field.A very tricky SQL Injection code may also be tried. I would like to mention, that in my career I have not encountered any case when there was ‘Internal Server Error' message as a result for the sign, but at times the fields did not react for more complicated SQL code.
Therefore checking for SQL Injection with single quote ‘ is quite a trustworthy way to check if this attack is possible or not.If the single quote does not return any inappropriate result, then we can try to enter double quotes and check the results.Also, SQL code for changing the query to always true can be considered as a way to check if this attack is possible or not. It closes the parameter and changes the query to ‘true‘. Therefore if not being validated, such input can also return any unexpected result and inform the same, that this attack is possible in this case.Checking for possible SQL attack can also be performed from the website‘s link. Suppose we have a website‘s link as In this case ‘books‘ is a parameter and ‘1‘ is its value. If in the provided link we would write ‘ sign instead of 1, then we would check for possible Injection.Therefore link will be like a test if SQL attack is possible for the website or not.In this case, if link returns an error message like ‘Internal Server Error‘ or a blank page or any other unexpected error message, then also we can be sure, that SQL Injection is possible for that website.
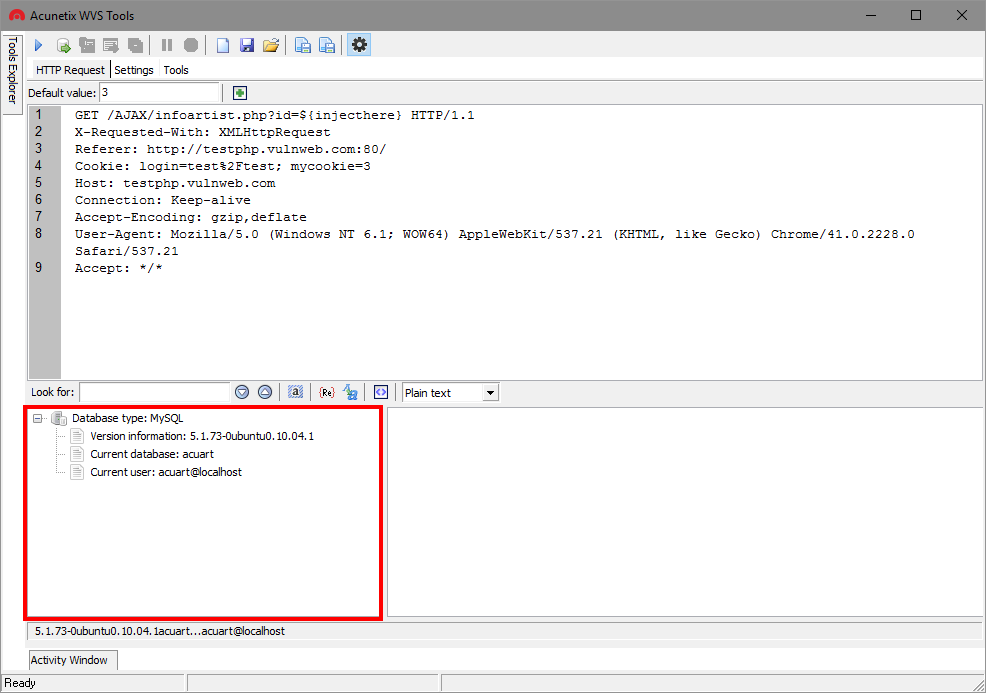
Later, we can try to send more tricky SQL code through the website‘s link.To check if this attack is possible through the website‘s link or not, code like ‘ or 1=1;– can also be sent.As an experienced software tester, I would like to remind, that not only the unexpected error message can be considered as a SQL Injection vulnerability. Many testers check for possible attack only in accordance with error messages.However, it should be remembered, that no validation error message or success message for malicious code can also be a sign, that this attack is possible. Security testing of web applications against SQL InjectionSecurity testing of web applications explained with simple examples:Since the consequences of allowing this vulnerability technique could be severe, it follows that this attack should be tested during the security testing of an application.
Now with an overview of this technique, let us understand a few practical examples of SQL injection.Important: This SQL Injection Test should be tested only in the test environment.If the application has a login page, it is possible that the application uses a dynamic SQL such as the statement below. Hi @Pooja,Code review (either manual or automated) is a good way to find the presence of hard-coded values (among other problems). Also, if you are familiar with the database design and can get access to the database, you may be able to find out the user information there.If you do not have any access to the application code or the database (in other words, you only have the website open in your browser), finding about hard coded user names may still be possible by noting the average times it takes to login with different user names. For example, if the username, Pooja, is hardcoded in the application it ought to log in faster than with another username, say Pooja1, which is present in the database. However, keep in mind that the success of this technique would depend on the assumption that most of the time in logging in is spent in validating the username and password. But, I think that it is worth a try.Inder P Singh.
SQL Injection TutorialLearn how SQL Injection attacks are achievedThis article covers the core principles of SQL injection. Specific attacks such as and are detailed in later articles of this tutorial and heavily rely on techniques exposed below.
If you are new to SQL injection, you should consider reading before continuing. WHERE Clause ManipulationUser supplied parameters frequently end up in the WHERE clause of dynamically built queries. Therefore, the only way to achieve a successful attack is to craft this segment of the query from vulnerable input. This can lead to powerful attacks when combined with other techniques, but WHERE clause manipulation is frequently used in its most basic form for login bypass or fast testing.Numeric parameters can also be vulnerable to SQL injections as explained in the article. This is possible because weakly typed languages like PHP do not force variables to keep their initial data type. As a result, it is possible to insert a crafted SQL statement in any vulnerable parameter to make a SQL injection attack. After determining the expected data type, the attack can be performed in a similar way it would have been with a vulnerable string parameter.

Direct InjectionDirect injection is possible in a vulnerable numeric parameter. It does not require quotation escaping and the crafted SQL segment can be inserted right after the parameter value. Even though it is the simplest case of SQL injection, examples with string parameter are far more popular since injecting string into numeric fields is confusing. Here is what an attack might look like in this situation. Get parameter value without sanitizing.$value = $GET'id';Build query – Note that 'productid' column type is INTEGER.$query = 'SELECT id, name, description FROM products WHERE productid= $value'; Quoted InjectionIn this case, the vulnerable parameter is surrounded by quotes. At first sight it might seems that quoted injections are limited to string parameters but it could also be used with a date or some DBMS specific type where quotes are used to define the value. To make things simpler those types are grouped under the name of string parameters.
The attack will almost be identical to the direct injection; the only difference is that the ending quote must be handled by the malicious parameter in order to create a valid query. Below is an example of a successful attack. Get parameter value without sanitizing.$value = $GET'cat';Build query – Note that 'category' column type is STRING (or VARCHAR).$query = 'SELECT id, name, description FROM products WHERE category=' $value';SQL injection Using UNIONThe UNION operator allows the attacker to extract sensitive information from the database. In most cases, the crafted SQL segment is submitted to the database engine via a WHERE clause manipulation. To achieve a successful attack, the parameter must end the original query and contain a UNION operator followed by a valid query.A common practice when using this technique is to make sure the WHERE clause of the first query is always false. That way, the data returned by the first query is eliminated and the results only contain data returned by the injected query.The main challenge for the attacker is to create a valid query after the UNION operator.
Both queries (before and after UNION) must have the same structure, otherwise an error will be raised by the database engine. Because the first query’s structure is ignored and database’s table names are unknown by the attacker, he will have to gather some information before achieving a successful attack.
Wwe 2k15 game free download. Open Daemon Tools and Mount Image the CD3. Download complete game with torrent software2. If you are facing problem in downloading, then see this page: This will teach you how to download data from my website:If you are facing problem in installing WWE 2K15, then please follow these instructions.1. Run setup and install game4.
Techniques to find this information are explained in the article, but for now let’s suppose we are given a valid query to simplify the example below. The script here is the one shown in the last example. User input' AND 'a'='b' UNION SELECT 999, 'abc', 'xyz' FROM members WHERE 'a'='aGenerated querySELECT id, name, description FROM products WHERE category = ' ' AND 'a'='b' UNION SELECT 999, 'abc', 'xyz' FROM members WHERE 'a'='a'Instead of returning products, the crafted query returns usernames and passwords of all members in the database. Let’s take a look at what was been done in this example. First, the WHERE clause is altered in order to make sure the first query never returns data as recommended earlier. The second query is then integrated with the UNION operator. Finally, the query is terminated by taking care of the quote that is left over with a true condition. Input IntegrationMost common cases have been explained, but examples presented up to now do not cover all possible scenarios of user input integration into SQL queries.
Let’s just think about UPDATE and INSERT statements. A vast majority of them are built dynamically according to information supplied by the user. Later articles of this tutorial explain how vulnerabilities present in those statements can be exploited.Uncommon user input integration should also be considered when searching for vulnerabilities. Every section of a query could be defined by user supplied parameter. For example, a column name integrated directly in the ORDER BY clause of a SELECT statement could be vulnerable to SQL injection.
Possibilities are endless and when shortcuts are used by programmers to quickly develop functionalities, we often see security flaws appear Some Cases Are Dead EndsOf course, all parameters are not vulnerable to SQL injection. But it is possible that a vulnerable parameter is integrated in some way that it would be impossible to make a successful attack. Such a situation could happen when the user input is partially sanitized or when it gets integrated into a complex sub query.